Prefer the old Management Library design instead?
or use our toggle button in the Menu
Find the Right Business Solutions
Search for answers to your business questions and software solutions to take your work to the next level.
The Best Executive Resume Writing Services (April 2025)
Executive resume writing businesses pride themselves on ensuring maximum customer satisfaction. A well-written resume should increase the volume of interested calls from hiring managers. This equates to more interviews and ultimately improves the possibility of landing desired roles. Most businesses provide more than one service. They’ll have a specialist writer(s) who will create an engaging …
12 Best Business Checking Accounts of April 2025
Juggling all the components of a business is no easy task. When dealing with finances, a standard bank account simply won’t cut it. The best business checking accounts go beyond traditional banking, providing several tools to help manage your finances while offering a number of features to help you keep everything in the air. Best …
10 Best States for Starting a Business – Where to Launch Your Startup
According to the US Bureau of Labor Statistics, around 47 million people quit their jobs in 2021. Then, roughly 5.4 million new business applications were filed, a 53% increase from 2019. If you’re thinking about joining this entrepreneurial club, several crucial decisions lie ahead. Below are the best states for starting your business. The Best …
What Is Supply Chain Management & How It Drives Efficiency
Supply Chain Management (SCM) is the backbone of any successful business. It ensures the efficient flow of goods, services, and information from suppliers to customers. By managing everything from raw materials to finished products, SCM is crucial in reducing costs, increasing efficiency, and meeting customer demands. This article aims to explain the fundamentals of SCM, …
15 Best Project Management Conferences in 2025
Every year, project management conferences come with a promise of learning and networking opportunities for project management professionals. The good news is that this year is no exception. If you have been looking forward to the next big event, here is a comprehensive list of the top project management conferences in 2023. Interest in Project …
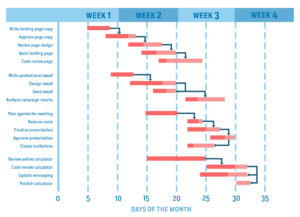
How to Use a Gantt Chart in 9 Steps
Gantt charts are a popular and time-tested way of visualizing project workflows. But they’re not just for any project. This project visualization approach aligns with the waterfall methodology that focuses on completing a task or process before the next one can begin. A Gantt chart lets you organize a project’s timescale and create an overview …
What is a Gantt Chart?
A Gantt chart is a project management tool used to visualize a project plan. It’s a useful way of showing scheduled tasks and task due dates. Gantt charts help team members and project managers view the start dates, end dates, and milestones of a project in one simple stacked bar chart. What is a Gantt …
What Is the Purpose of Operations in a Business?
Business operations is an elusive but necessary part of any organization looking to maximize productivity and profit potential. Companies that struggle to understand operational demands often miss key opportunities to succeed. This article explains how operations applies to businesses and tips for improving efficiency across the board. What Are Operations in a Business? An operations …
PRODUCT REVIEWS
EVALUATE YOUR
How Much Do TikTok Ads Cost? 2024 Pricing Explained
TikTok took its time to start a proper ad program, which pushed brands to find other ways to get noticed on the app. This led influencer marketing and branded promotions to take off on TikTok. While TikTok began to try out advertising in 2020, it wasn’t until 2022 that their ad efforts picked up steam. …
How Much Does TV Advertising Cost? 2024 Update
Discover how much TV advertising costs and what factors affect pricing. Learn how to maximize your ad budget and reach your audience effectively today!
How Much Does It Cost To Advertise On Google?
Is your business considering advertising on Google, but you need clarification on the costs? How much should you budget for a successful Google Ads campaign? In this comprehensive guide, we delve into the factors that influence the cost of Google Ads, provide industry-specific cost insights, and offer expert tips on budgeting, bidding, and optimizing your …
How to Advertise Your Business on Facebook Beginners Guide
Facebook, the social media behemoth, has become an essential marketing tool for businesses of all sizes. With billions of active users worldwide, Facebook provides a vast audience for your business. However, tapping into this pool of potential customers requires a comprehensive understanding of Facebook advertising. This article will serve as a beginner’s guide on advertising …
Marketing Mix: Traditional 4Ps to Evolution of Marketing 7Ps
The marketing mix, often referred to as the 4Ps of marketing, remains a foundational model in marketing. This model was first introduced by E. Jerome McCarthy in 1960 and has since been expanded to include three additional elements, known as the 7Ps of marketing. As businesses navigate the complexities of modern markets, understanding and effectively …
PRODUCT REVIEWS
EVALUATE YOUR
Employee Incentive Ideas: Boost Motivation & Retention
Employee incentives play a vital role in boosting motivation, increasing engagement, and improving retention within the workplace. A well-designed incentive program shows employees their contributions are valued, fostering loyalty and productivity. These programs can address various needs, from financial rewards to personal growth opportunities. Incentives fall into three major categories: monetary (e.g., bonuses, raises), non-monetary …
How to Find a New Job 2025: Top Tips & Effective Strategies
Assessing your career goals and interests is essential to beginning your job search. Reflect on what you want from your next role, such as the position, industry, company size, or the importance of work-life balance. Identify your core skills, strengths, and areas for improvement. Consider how these factors align with your long-term career aspirations. Consider …
How to Describe Your Work Style in an Interview: 2024 Guide
Self-awareness of your work style is crucial for achieving career success. Knowing how you approach tasks, solve problems, and collaborate with others can help you thrive in different work environments. This understanding improves job performance, enhances team dynamics, and helps you align with company culture. In interviews, articulating your work style gives you an edge …
What Is Headhunting: How It Works & Why It Matters
Headhunting is a specialized recruitment strategy focused on identifying and approaching highly skilled professionals, particularly those not actively seeking new job opportunities. Unlike traditional recruitment, which often relies on job postings and applications, headhunting targets top-tier talent through direct outreach and networking. Headhunters use targeted methods like networking, industry research, and direct outreach to connect …
The Ultimate Guide to State Corporate Tax Rate
Corporations are responsible for a bevy of taxes on the state level across different mediums. Above that, each state sets its own rates for corporate entities to contend with. State corporate tax rate varies depending on which state from which you operate your business. Corporate State Tax Rates Explained Corporations are a type of business …
PRODUCT REVIEWS
How to Register a Business in California: Guide 2025
Enter the realm of California, where endless possibilities and an entrepreneurial spirit abound. Here, dreams soar, and businesses thrive under the golden sun. Starting a new business is an exciting adventure, but the registration process can leave even the most passionate entrepreneur feeling lost. Fear not, ambitious dreamers of California! This blog post will illuminate …
How to Start a Business With No Money & Minimal Resources
Many people believe that starting a business requires significant capital, but this is a common misconception. You can overcome financial barriers and launch a successful venture with creativity, resourcefulness, and strategic planning. Leveraging your skills, using free resources, and starting small make it possible to build a profitable business even with minimal upfront costs. The …
How to Start a Recruiting Business: A Beginner’s Guide
The demand for professional recruiting services is growing as businesses seek top talent to drive their success. Starting a recruiting business offers a lucrative opportunity to connect companies with qualified candidates while addressing their hiring needs. This business model provides flexibility to work from anywhere, scalability to grow your operations, and the ability to specialize …
How to Start a Bookkeeping Business From Scratch in 2025
The demand for bookkeeping services is rising as businesses of all sizes seek to manage their finances effectively. Starting a bookkeeping business presents a fantastic opportunity to tap into this growing market while offering valuable expertise to clients. This business model is beautiful due to its flexibility, low startup costs, and potential for scalability. Whether …
How to Start a Photography Business From Scratch in 2025
Professional photography is in high demand as individuals and businesses seek high-quality visuals for personal and commercial needs. Starting a photography business is an excellent opportunity for creative entrepreneurs to turn their passion into a profitable venture. It offers flexibility to work on your terms, the creative freedom to explore your artistic style, and significant …
PRODUCT REVIEWS
5 Best North Carolina Credit Repair Companies in 2025
Improving your credit score is a vital step toward achieving financial stability, and in North Carolina, credit repair services play a key role in educating members on how to do so. Whether you’re applying for a loan, renting a home, or even job hunting, a strong credit score can open doors and reduce financial stress. …
5 Best Atlanta Credit Repair Companies in 2025
In a dynamic city like Atlanta, where ambition meets opportunity, maintaining a strong credit score is key to unlocking both personal and professional milestones. Credit Repair Atlanta is committed to helping residents take control of their financial future by identifying and resolving credit challenges with care and precision. Partnering with top credit repair companies such …
8 Best Banks for Small-Business Loans to Consider in April 2025
Small business loans provide funding for business owners to run and grow their companies. These loans can be obtained from traditional banks, credit unions, and online lenders. Usually, the funds are given as a lump-sum payment and repaid monthly unless the lender specifies otherwise. In this guide, we’ve reviewed the top banks for small-business loans, …
Grasshopper Bank Review: Features, Fees, & Customer Feedback
If you’re a small business owner seeking a reliable checking account for your finances, Grasshopper Bank offers a business checking account designed just for that. They provide various perks and services tailored for small businesses. Below, you’ll find details on the benefits of Grasshopper Bank accounts and their services to help you choose a business …
Is Chime a Real Bank or Fintech & How Does It Work
Chime is a popular financial technology (FinTech) company that offers digital banking services through its mobile app. While it doesn’t operate as a traditional bank with physical branches, Chime partners with FDIC-insured banks to provide secure banking services. This partnership allows Chime customers to access checking and savings accounts, debit cards, and other financial tools. …
PRODUCT REVIEWS
How to Land a 6-Figure Job: A List of High-Paying Careers
Landing a 6-figure job is a common goal for many professionals who aspire to financial security, career growth, and personal fulfillment. These high-paying roles are often found in industries that demand specialized skills, advanced education, and significant experience. However, reaching this income level is about more than luck. It requires strategic career planning, qualifications, and …
What Is Product Management: Strategies, Functions, & Tools
Product management involves overseeing the entire lifecycle of a product, from its initial concept to market launch and beyond. A Product Manager (PM) ensures the product meets customer needs, aligns with the business’s goals, and remains competitive. They act as the glue between engineering, marketing, and design teams, working to deliver a successful product. Effective …
How long should your resume be
Resume length is a contention among recruiters, professional resume writers, and human resources experts. However, most people agree that a resume should not be ten pages long, even if you are an Elon Musk type. Ok, Elon Musk could get away with it, but the rest of us not! You can only imagine hiring managers’ …
The Ultimate Guide: How Do You Describe Yourself to a Future Employer
Understanding the “Describe Yourself” Question In many job seekers’ experiences, there are some questions during an interview that are more common than others. One of these questions is, how would you describe yourself? While it may be evident to some of what you shouldn’t say, you may be surprised at how many job seekers give …
After the Interview Sample Thank You Letters
Job interviews are an intense and often nerve-wracking process that requires preparation, confidence, and a clear understanding of the role and company. Once the interview is over, following up with a thank you letter is crucial. This blog explores the importance of thank you notes after job interviews, offers practical guidance on writing them, showcases …
PRODUCT REVIEWS
EVALUATE YOUR